In May 2017, a significant cyberattack known as WannaCry swept across the globe, impacting over 150 countries and infecting approximately 230,000 computers. This event marked one of the largest ransomware attacks in history, highlighting vulnerabilities in cybersecurity and the need for robust defense mechanisms.
Understanding Ransomware
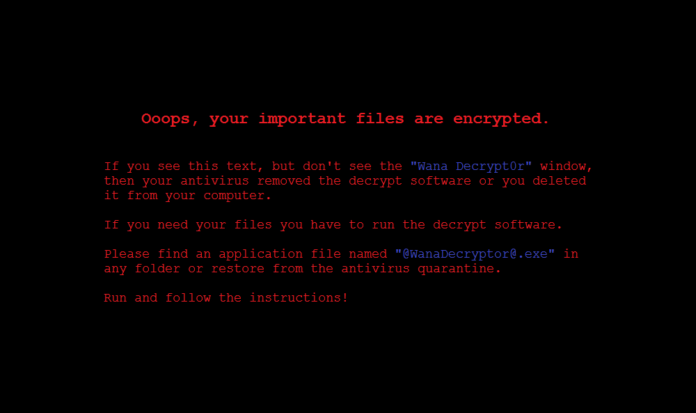
Ransomware is a type of malicious software that encrypts a victim’s files, rendering them inaccessible until a ransom is paid. WannaCry utilized a unique propagation method, allowing it to spread rapidly and infect a vast number of systems in a short time.
How WannaCry Works
WannaCry operates by exploiting vulnerabilities in the Server Message Block (SMB) protocol, particularly through a flaw known as EternalBlue. This vulnerability allowed it to execute arbitrary code on vulnerable systems, enabling the ransomware to spread without user interaction.
Once a computer is infected, WannaCry encrypts files and displays a ransom note demanding payment in Bitcoin. The ransom typically started at $300, increasing to $600 after three days. The attackers claimed that if the ransom was not paid within seven days, files would be lost permanently.
The Timeline of the Attack
The attack began on May 12, 2017, with the first known infection originating from a Southeast Asian Internet Service Provider (ISP). Within hours, WannaCry had spread to numerous other ISPs across Asia, Europe, and Latin America. By the end of the first day, the ransomware had affected systems in 74 countries.
Propagation Mechanism
WannaCry’s rapid spread was due to its worm-like capabilities. It could scan for other vulnerable computers on the same network and infect them without any user interaction. This feature distinguished it from other ransomware types, which typically rely on phishing attacks to trick users into executing malicious files.
The Role of the NSA and the Shadow Brokers
The origins of the WannaCry attack trace back to a leak of hacking tools from the National Security Agency (NSA) by a group known as the Shadow Brokers. These tools included EternalBlue, which was developed by the NSA to exploit vulnerabilities in Windows systems but was never disclosed to Microsoft, leaving many systems exposed.
On April 14, 2017, the Shadow Brokers released the exploit, which would soon be used to facilitate the WannaCry attack. This incident raises significant questions regarding the responsibility of the NSA and the ethical implications of stockpiling vulnerabilities.
The Accidental Hero: Marcus Hutchins

Amid the chaos, a British security researcher named Marcus Hutchins inadvertently halted the attack by registering a domain that WannaCry was trying to contact. This action acted as a “kill switch,” stopping the ransomware from spreading further. Hutchins’s quick thinking and technical expertise played a crucial role in mitigating the damage of the attack.
The Aftermath of WannaCry
In the wake of the attack, it was reported that the NHS in the UK was one of the most severely affected organizations, with over 70,000 devices impacted, resulting in significant operational disruptions. Globally, the attack caused damages estimated between $4 billion and $8 billion.
Understanding the Impact
Despite affecting a vast number of computers, the attackers reportedly only received around $130,634 in ransom payments. This discrepancy highlights the skepticism surrounding the effectiveness of paying ransoms, as many victims who paid did not regain access to their files.
The Importance of Cyber Hygiene
The WannaCry incident serves as a stark reminder of the importance of maintaining updated systems and implementing robust security measures. Organizations must prioritize regular software updates, employ effective backup strategies, and educate employees about cybersecurity risks.
Lessons Learned
The attack underscored the need for a proactive approach to cybersecurity. Organizations should not only focus on reacting to attacks but also on preventing them through awareness and preparedness. Regular training, updates, and a well-defined incident response plan can significantly reduce the risk of future attacks.
Conclusion
The WannaCry ransomware attack was a pivotal moment in the realm of cybersecurity, revealing vulnerabilities that can be exploited by malicious actors. As we move forward, it is crucial to learn from these events and adopt more secure practices to protect against future threats. The rise of ransomware attacks, particularly during the digital transformation accelerated by the COVID-19 pandemic, necessitates a vigilant and informed approach to cybersecurity.
In conclusion, the WannaCry attack serves as a critical case study for understanding the complexities of ransomware and the importance of cybersecurity in our increasingly digital world. By implementing stronger security measures and fostering a culture of awareness, organizations can better protect themselves against the evolving landscape of cyber threats.